Operations Security.

DeFi is roaring with extraordinary annual percentage yields, and people are rushing to put their money in different protocols with the expectation of hefty rewards. In the atmosphere of a gold rush, it’s easy to get carried away and forget about essentials like security.
When you go decentralized, you are in control. I once shared this meme, and this is the perfect time to repost it.

Crypto is generous but dangerous. If you make a mistake, many times there’s no going back. You can’t call support and ask to fix anything—there is no support. Moreover, blockchains are immutable. Send one wrong transaction and you’ll never see that money again.
Today, however, I want to talk about something even bigger. Even if you control your on-chain activity, double-check addresses and do due diligence on projects before ‘aping’ into them, it still may not be enough.
Throughout 2020, we witnessed numerous DeFi platforms suffer from hacks and exploits. Often, the integrity of the platform people were using was fine, but the other apps it connected with were compromised, which led to undesired and unexpected outcomes.
Even high-profile crypto users, some of whom run crypto startups, had their wallets hacked and stolen funds. If crypto OGs and builders aren’t safe, you aren’t either.
SoI want to give you a briefing on basic operation security. By following these simple rules, you can minimize potential risks.
How to Store Crypto
This seemingly simple question can make you realize that you are most likely doing it wrong. Crypto makes you a bank, and banks take custody very seriously. So should you.
Before we continue, let me remind you that any crypto wallet has a public key (wallet address) and a private key. Private keys are usually long alphanumeric strings, which are hard to memorize. Hence, private keys can be represented by 12, 24, or any other sequence of words called a ‘mnemonic phrase.’
You shouldn’t ever reveal your private keys or mnemonic phrases to anyone. Sometimes, scammers will make it look like you need to provide this information for security purposes. This is called phishing, and they’re trying to scam you, so stay alert.
Furthermore, you shouldn’t store your private key files or mnemonic phrases online. That means avoiding cloud storage like Google drive or Dropbox. The ideal and most secure way is to memorize your mnemonic phrase, but if you have multiple wallets, that’s probably testing the limits of your memory. Never enter mnemonic phrases into any text file on your computer or phone; write them down on a physical piece of paper so no one can have access to them.
Now, let’s distinguish between the types of wallets. Typically, you would have a cold and a hot wallet.
A cold wallet is for your long-term holds. This is your citadel, and you should minimize transfers to and from it.
The most popular type of cold wallets are hardware wallets like Ledger and Trezor. They are small physical devices, which interact with dedicated software on your computer to access your crypto to receive and send coins.
The hardware part is locked by a pin code. It obfuscates all your private data, including the wallet’s private keys. Hence, without access to your physical hardware and knowledge of the pin, no one can access your funds, even if your computer is compromised.

Source: Trezor.
Hardware wallets are protected by the master mnemonic phrase. Exercise the same precautions as with any other mnemonic phrases. Avoid storing them in a digital format at all costs.
The cold wallets I just described aren’t 100% secure since they are somehow connected to the internet. There’s a meager chance something can go wrong with such a wallet if used correctly. However, if you want to make your wallet unhackable, you can take it offline completely, albeit a ‘how to’ about that is beyond the scope of this briefing.
Hot wallets are for your daily activities. The most important rule when using them: don’t store too much there.
When you make transactions and use services, you create a digital fingerprint, which scammers can use to target you. Hence, there’s a higher chance your hot wallet can be compromised.
Which currency you are using is also important. If you are using a smart-contract platform, you will need to exercise additional precautions.
Staying Safe in DeFi
A lot can go wrong when you use decentralized applications on platforms like Ethereum or Binance Chain. Let’s review a couple of potential causes.
The most unanticipated way users lose their crypto is by having unreviewed approvals to various smart contracts. In short, smart contracts can’t just take money from your wallet if they get compromised.
If you’re using DeFi, chances are you are using Ethereum or compatible smart contracts like those living on Binance Smart Chain. The most popular tool for such interactions is Metamask.
When you are doing transactions, you would often be prompted to approve spending tokens from your account. It’s not like you are sending money to a smart contract, rather, it takes money from you with your permission.
If you don’t control these permissions, things can go bad. A hacker can potentially drain your wallet. By the time you notice it might be too late.
The most common solution is only to approve the exact amount of money you’re planning to spend. However, many platforms will force you to make an infinite approval, which opens up attack vectors.
I suggest using Revoke for regularly reviewing and revoking approvals. If you hear the news that the platform you used before is hacked, immediately go to Revoke to protect your funds.
Furthermore, your Metamask or any other wallet can be compromised. Keep in mind that web wallets often are integrated with other software like your browser. When you visit various websites, hackers can somehow mess with your wallet and steal your money.
One example is the recent hack of a Metamask wallet that belonged to the CEO of Nexus Mutual, a prominent decentralized insurance platform. The hacker substituted the destination address with their own and stole $8 million.
To protect from potential wallet hacks, make sure that you download software from legitimate sources. For Metamask, go to the Consensys website and search for Metamask there.
Second, when using crypto software, strive to avoid visiting websites that you don’t know much about. Also, if a website doesn’t have a security certificate, it’s a major red flag.
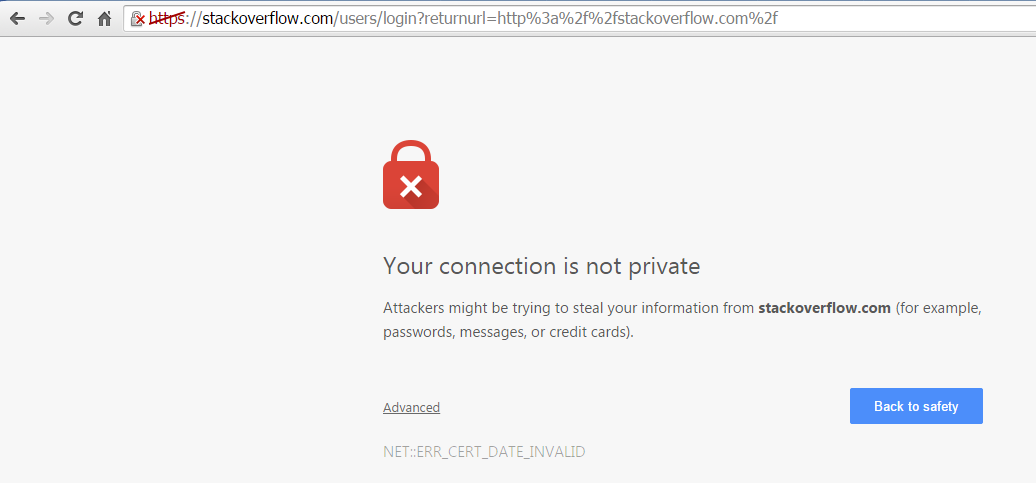
Privacy Error, close this website immediately. Source: SuperUser.
There are numerous other attack vectors, and it’s impossible to review them all. The rule of thumb here is to only go to websites you know and pay attention to every step you do when interacting with smart contracts.
If you stay vigilant, you will make it much less likely that you will lose funds to a hack or simple mistake. You are your own bank, so act accordingly.
